Archive
Researchers crack the world’s toughest encryption by listening to the tiny sounds made by your computer’s CPU

Security researchers have successfully broken one of the most secure encryption algorithms, 4096-bit RSA, by listening – yes, with amicrophone — to a computer as it decrypts some encrypted data. The attack is fairly simple and can be carried out with rudimentary hardware. The repercussions for the average computer user are minimal, but if you’re a secret agent, power user, or some other kind of encryption-using miscreant, you may want to reach for the Rammstein when decrypting your data.
This acoustic cryptanalysis, carried out by Daniel Genkin, Adi Shamir (who co-invented RSA), and Eran Tromer, uses what’s known as a side channel attack. A side channel is an attack vector that is non-direct and unconventional, and thus hasn’t been properly secured. For example, your pass code prevents me from directly attacking your phone — but if I could work out your pass code by looking at the greasy smudges on your screen, that would be a side channel attack. In this case, the security researchers listen to the high-pitched (10 to 150 KHz) sounds produced by your computer as it decrypts data.
This might sound crazy, but with the right hardware it’s actually not that hard. For a start, if you know exactly what frequency to listen out for, you can use low- and high-pass filters to ensure that you only have the sounds that emanate from your PC while the CPU decrypts data. (In case you were wondering, the acoustic signal is actually generated by the CPU’s voltage regulator, as it tries to maintain a constant voltage during wildly varied and bursty loads). Then, once you have the signal, it’s time for the hard bit: Actually making sense of it.

Here you can see the frequency spectrogram of various CPU instructions (down the right hand side)
Without going into too much detail, the researchers focused on a very specific encryption implementation: The GnuPG (an open/free version of PGP) 1.x implementation of the RSA cryptosystem. With some very clever cryptanalysis, the researchers were able to listen for telltale signs that the CPU was decrypting some data, and then listening to the following stream of sounds to divine the decryption key. The same attack would not work on different cryptosystems or different encryption software — they’d have to start back at the beginning and work out all of the tell-tale sounds from scratch.
The researchers successfully extracted decryption keys over a distance of four meters (13 feet) with a high-quality parabolic microphone. Perhaps more intriguingly, though, they also managed to pull of this attack with a smartphone placed 30 centimeters (12 inches) away from the target laptop. The researchers performed the attack on different laptops and desktops, with varying levels of success. For what it’s worth, the same kind of electrical data can also be divined from many other sources — the power socket on the wall, the remote end of an Ethernet cable, or merely by touching the computer (while measuring your body’s potential relative to the room’s ground potential).

In this light-weight setup, only the microphone (B) needs to be positioned correctly — everything else could be hidden away, for stealthy snooping
In terms of real-world repercussions, acoustic cryptanalysis is actually surprisingly dangerous. Imagine if you were decrypting some files in a library, coffee shop, or other public space — someone could obtain your decryption key just by placing their phone near your computer. Alternatively, an attacker could use spear phishing to put malware on yourphone that listens for the decryption key. With HTML5 and Flash able to access the microphone, it would be possible to build a website that listens for encryption keys too. The researchers propose one particularly nefarious scenario: Put a microphone into a co-located server, slot it into a rack in a data center, and then scoop up the encryption keys from hundreds of nearby servers.
If you want to keep your data secure, you only really have two viable options: Heavy-duty encryption, physical security, and ideally both at the same time. If an attacker can’t get physically close to your data, it instantly becomes much harder to steal it. As far as mitigating acoustic cryptanalysis attacks, you either implement physical security — keep your laptop in a sound-tight box, or never let anyone near your computer when you’re decrypting data — or you need to use a “sufficiently strong wide-band noise source.” Something like a swooping, large-orchestra classical concerto would probably do it.
Research paper: RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis [PDF]
Why Is Google Buying So Many Robot Startups?
Forget robotic product delivery. As usual for Google, I suspect it’s all about the data.
Image : Google-bot – The M1 Mobile Manipulator from Meka, one of several robot companies acquired recently by Google.
Google has quietly bought seven robotics companies, and has given Andy Rubin, the man who originally led the Android project, the job of developing Google’s first robot army. And so, theNew York Times suggests it might only be a few years before a Google robot driving in a Google car is delivering products to your door.
I somehow doubt Google has anything quite so futuristic in mind. I think the effort is quite similar to both Google’s self-driving car endeavor and its Android project. In other words, it’s all about gaining a dominant position in markets where data is about to explode.
Take Google’s self-driving cars. Contrary to common perception, the company didn’t “invent” this technology; most carmakers were already working on autonomous system when Google got involved, and academic researchers had made dramatic recent progress—propelled in large part by several DARPA challenges (see “Driverless Cars are Further Away than You Think”). Google just saw that this was where the automotive industry was headed, and realized that the advent of automation, telematics, and communication would mean a tsunami of data that it could both supply and profit from. Given that many of us spend several hours a day in automobiles, this data could help Google learn more about users and tailor its products accordingly.
Similarly, I suspect Google has recognized that a new generation of smarter, safer, industrial robots is rapidly emerging (see “This Robot Could Transform Manufacturing” and “Why This Might be the Model-T of Workplace Robots”), and it’s realized that these bots could have a huge impact both at work and at home. Whoever provides the software that controls and manages these robots not only stands to make a fortune by selling that software; they will have access to a vast new repository of data about how we live and work.
In this sense, I think Google is being true to its stated mission: “to organize the world’s information”—although it’s worth noting that in an increasingly connected and data-rich world that could mean seeking to organize just about every aspect of our lives. Luckily for Google, it may soon have a robot army to help it keep everything in order.
written by: Will Knight
One Coin To Rule All Your Credit Cards
There are many digital wallet systems that work with our smartphones today, but sometimes, having the physical card to swipe at the counter can be more convenient and takes much less time. Besides, not all shops will accept the type of digital wallet you use. That said, lugging around your credit cards, debit cards, ATM cards, gift cards, etc can be a drag.
We have here a handy alternative called Coin.
Despite its name, Coin is a card, and it carries a magnetic stripe like all your other cards. It works like them too — you can swipe or scan it like you would your loyalty cards, membership cards, credit cards etc when you make your purchases. The difference is, you just need this one master card to do it all.
Inserting Card Information
To use Coin, first you need to insert your card information into it. To do this, you’ll need its smartphone app (available on iOS and Android) along with a smartphone credit card reader.
Just swipe your card through the reader (dongle) and take a picture of the front and back of that card. The information will be sent to Coin via Bluetooth 4.0 and you can store as many cards as you want.

To use a card on a purchase, select the appropriate card to use via the button on Coin. Coin will display the cards you have stored in there one at a time. Pick the card you want and swipe away.
According to the official website, the card selector button is stiff, which means that no accidental card changes will occur when you hand it over to the cashier.
Security Features
You might feel that the idea to store the details of all your cards in Coin a little unsafe, but there are a few built-in security features that can help ease your mind.
Coin is paired to your smartphone with Low Energy Bluetooth 4.0. Whenever it gets separated too far away from your smartphone, an alarm will be triggered to notify you that your Coin has been misplaced.

If Coin gets stolen and leaves the connectivity period of your smartphone for too long, it willautomatically deactivate itself, rendering it useless. How far or how long Coin is separated before this is triggered can be set via the app.

Your online Coin account, mobile app and the device itself use 128-bit or 256-bit encryption for all storage and communication to ensure your card information is safe. Coin also doesn’t display your entire credit card number — together with its encryption, this makes it harder for your card to get skimmed.
Limitations
Batteries in Coin can last around two years of daily usage, and you will have to replace it with a new one if you want to continue using Coin. Coin can work outside of the U.S. but users are advised to bring their cards as backup, just in case. Coin does not support chip and pin cards, however, future generations of Coin will include EMV.

Coin is available in two colors (Snow and Midnight), and is currently available for pre-order at a price of $55 (inclusive of shipping fee). It will reach you during the summer of 2014. The current introductory price of $55 is limited to early birds as Coin will retail at $100.
Source: Hongkiat
Android vs. iPhone: Which Should You Buy?

by Eric Larson on http://www.mashable.com
Thomas Edison vs. Nikola Tesla. Roger Federer vs. Rafael Nadal. Amanda Bynes vs. Twitter.
The world is full of great rivalries, and for smartphones, there are no exceptions. The iPhone vs.Android debate is a staple within the tech community; most users will loyally (and outspokenly) tell you why their respective devices, and theirs only, are the far superior choices.
But what if you haven’t decided? Maybe you’re impartial to both. Maybe you’re still clutching yourNokia brick. Or maybe you just don’t care.
In any case, we’ve highlighted components of both phones to help you decide which brand is right for you. It boils down to minor preferences: Would you rather have an operating systemthat’s open-source? Or a more compact device likely to get top apps sooner? Et cetera.
Different strokes for different folks, really. Take a look and tell us in the comments which one you prefer — but please, be gentle.
1. Android: Open-Source Operating System
Unique to Android phones is its powerful open-source operating system, which is the most popular in the world, according to data by Kantar Worldpanel ComTech. The system lets manufacturers, carriers, independent developers and savvy consumers modify content and fix bugs — all via the code Google releases under a free software permit called the Apache License.
The freely amendable OS opens up the potential for cool system projects, too, likeCyanogenmod, Paranoid Android and MIUI. It also allows developers to distribute and sideload content outside the constraints of the Google Play store.
2. iOS: Apps
Image: iTunes and Google Play
Apps, on the other hand, are a different story. For years, iOS lead the way with highest number of available apps, but now the numbers seem to be changing. An Apple press release from June, 2013 says the iTunes Store has more than 900,000 apps; and a Google spokesperson confirmed to Mashable that the Play Store has more than 975,000.
The quality of the apps is obviously a subjective argument, and loyal users of both will argue why and how their platforms do them better. What’s not as subjective is availability. iOS inarguably gets apps sooner — it took months for Android to access Instagram and Vine, after all. While Android may be catching up, Apple still secures more big-name apps before any other platform.
3. Android: App Flexibility
On the flip side, Android offers more flexibility with its apps by allowing Firefox, Opera andChrome to run, a capability that isn’t permitted through iOS.
4. Android: Data-Sharing
Something often overlooked in Android, as highlighted by Computerworld, is a system-wide sharing function called “intents.” The feature lets you pass data — text, photos, links — in between your apps. To use it, tap and hold your finger on a sentence (say, from an email) and click the “Share” icon, which pulls up a list of apps that allow the function, like Gmail or Dropbox. From there, it’s as simple as dragging the text, or whatever else you’ve selected, into the app of your choice.
Because of Android’s open-source OS, any developer can program his or her app to correspond with the internal data-sharing. It may seem minuscule, but it makes tasks like sharing photos or Google searches undoubtably quicker.
5. iOS: Portability
When it comes to size, iPhones are smaller and easier to carry than most Android phones. TheiPhone 5, the tallest to date, is 4.87 inches tall and 3.95 ounces, compared to the HTC One‘s 5.41 inches and 5 ounces. The Samsung Galaxy S4 measures in at 5.38 inches in height and 4.59 ounces.
On the other hand, rumors are circulating that Apple may debut a bigger phone come September, the time of year it typically unveils new iPhones.
6. iOS: Consistency
One perk to not having an open-sourced system is consistency across devices. Small actions, such as turning on Wi-Fi, vary from the Nexus 4 to the Galaxy S4 to the HTC One — again, a result of different interfaces. The tradeoff, though, is that it gives you the potential to customize.
Most of Apple’s functions remain homogenous across devices — there’s really only one way to do something on the iPhone. Once you’re in the “ecosystem,” so to speak, you only need to remember one login password to sync your photos, music and other files across each device using iCloud.
Some argue the open-source method, particularly when it comes to the raw quality of its mobile devices, is Android’s double-edged sword: a stellar operating system that lacks a steady phone.Slate‘s Farhad Manjoo writes:
“These phones have the potential to be really wonderful machines, even as great as Apple’s flagship phone. But then, at the last second, the phone makers and the world’s cellular carriers snatch defeat from the jaws of victory. They ruin the phones’ potential with unnecessary features and apps that lower the devices’ battery life, uglify their home screens, and make everything you want to do extra annoying.”
If you’re someone who lives and dies by your Gmail account or Google+, however, Android’s strong ties with its properties might make for a better (and smoother) fit.
It’s a tough conclusion to draw. What made you choose your phone, and are you happy with that decision? What would it take for you to make the switch?
Viewfinder, an app from former Google folks, makes it easier to view and share iPhone photos
If your iPhone (s AAPL) camera roll is filled with thousands of photos, it’s tough to know which ones you’re looking for or share them with others. Viewfinder, an iPhone app created by former Google (s GOOG), Microsoft (s MSFT) and Dropbox employees, wants to make it easier to organize those photos and share and discuss them with others. A new version of the app launches on Tuesday.
“We want to be the Google for your personal life,” cofounder Spencer Kimball, who previously worked on systems and web app infrastructure at Google, told me.
Viewfinder uses photo metadata to sort and organize a user’s photos by time and place. Users can scroll through their photos with a dial or “long-press” the right side of the screen to move faster to a specific time.
Viewfinder also lets users share certain photos or collections of photos with specific groups of people…
View original post 276 more words
Codeanywhere raises $600,000 to boost its ‘Google Docs for developers’ service
Codeanywhere, one of a number of startups offering a service pitched as ‘a Google Docs equivalent for developers’, has raised $600,000 in funding from World Wide Web Hosting, LLC, the parent company of Site5 Web Hosting.
The startup offers a browser-based environment for coding in HTML, PHP, JavaScript, CSS, and XML, with a built-in FTP client and Dropbox support for storing files.
Codeanywhere faces competition from the likes of Cloud9 IDE andShiftEdit. However, co-founder Ivan Burazin says that Codeanywhere’s strength is in its simplicity. “You can think of us as an application that lets you code on any resource you have, whereas Cloud9 wishes to be a platform (on which) for you to code.”
Ben Welch-Bolen of World Wide Web Hosting adds, ”(Codeanywhere) focused on providing a simple tool that has a lot more mass market appeal whereas their competitors have started at the top of the market with too much complexity.”
Croatia-based Codeanywhere, which was known as PHPanywhere until 2011, will use the funds to improve scalability, acquire more users (the company currently boasts 150,000), and develop new features such as collaboration tools and native mobile apps. That said, Codeanywhere already supports mobile devices, albeit only as a Web app.
As for why a Web hosting firm invested in a browser-based coding startup, Welch-Bolen explains, “There is a race inside the hosting industry to make it easier to go from a development work environment to production with one click. For our hosting brands it made sense to work with Codeanywhere and try and find a solution that allows one click publishing of projects to a hosting platform.”
Header image credit : www.buzzle.com
Source: The Next Web
Increase of Smartphone Ownership 2013 – Study
by Aaron Smith on http://pewinternet.org

For the first time since the Pew Research Center’s Internet & American Life Project began systematically tracking smartphone adoption, a majority of Americans now own a smartphone of some kind. Our definition of a smartphone owner includes anyone who says “yes” to one—or both—of the following questions:
- 55% of cell phone owners say that their phone is a smartphone.
- 58% of cell phone owners say that their phone operates on a smartphone platform
common to the U.S. market.1
Taken together, 61% of cell owners said yes to at least one of these questions and are classified as smartphone owners. Because 91% of the adult population now owns some kind of cell phone, that means that 56% of all American adults are now smartphone adopters. One third (35%) have some other kind of cell phone that is not a smartphone, and the remaining 9% of Americans do not own a cell phone at all.
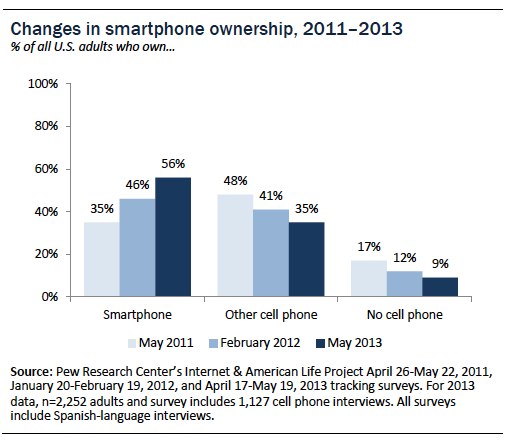
Demographic trends in smartphone ownership
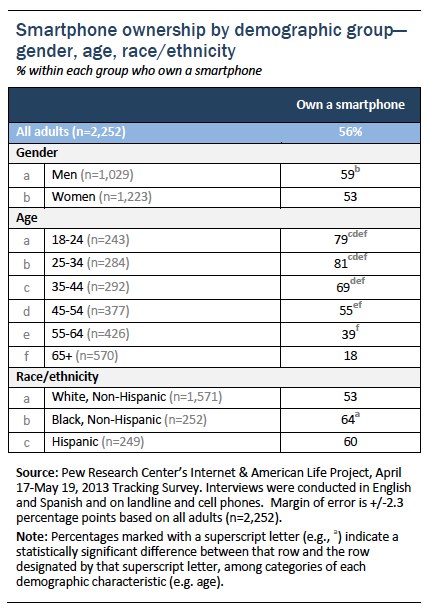
As has consistently been the case since we began measuring smartphone adoption two years ago, ownership is particularly high among younger adults, especially those in their twenties and thirties (although a majority of Americans in their mid-forties through mid-fifties are now smartphone adopters) and those with relatively high levels of household income and educational attainment.
Every major demographic group experienced significant year-to-year growth in smartphone ownership between 2012 and 2013, although seniors—defined as those 65 and older—continue to exhibit relatively low adoption levels compared with other demographic groups. Some 18% of Americans age 65 and older now own a smartphone, compared with 13% in February 2012.
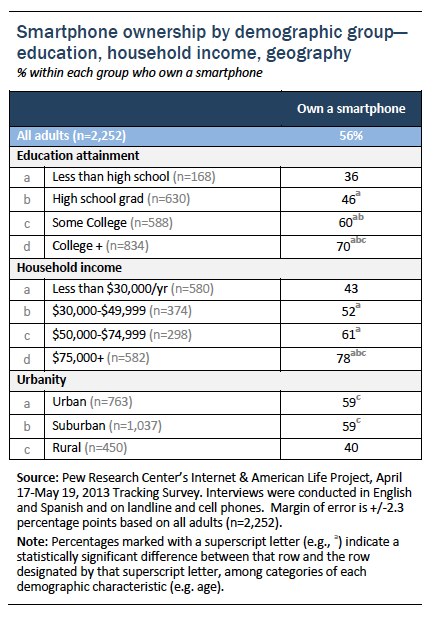
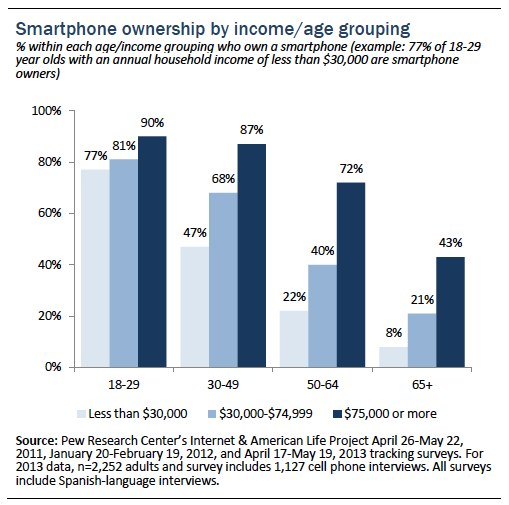
Though growth in smartphone ownership has occurred up and down the economic spectrum, adoption still varies significantly by household income. However, that variation is unevenly distributed across different age groups. Younger adults—regardless of income level—are very likely to be smartphone owners. Conversely, for older adults smartphone ownership is more of an “elite” phenomenon: smartphones tend to be quite prevalent at the upper end of the income distribution but much less common among those with lower income levels.
Trends in platform adoption
Since 2011, the proportion of cell owners who say they own either an iPhone or an Android device have each grown dramatically. Android owners now represent 28% of all cell owners (up from 15% in May 2011), while iPhone owners now represent 25% of the cell owner population (up from 10% in May 2011). Meanwhile, the proportion of cell owners who say they own a Blackberry device has fallen from 10% in May 2011 to just 4% in our most recent survey.
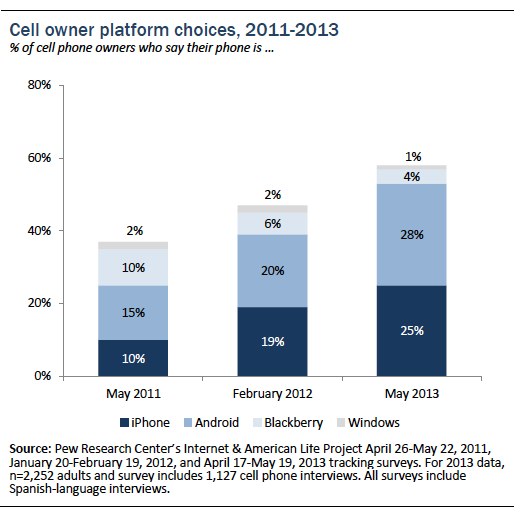
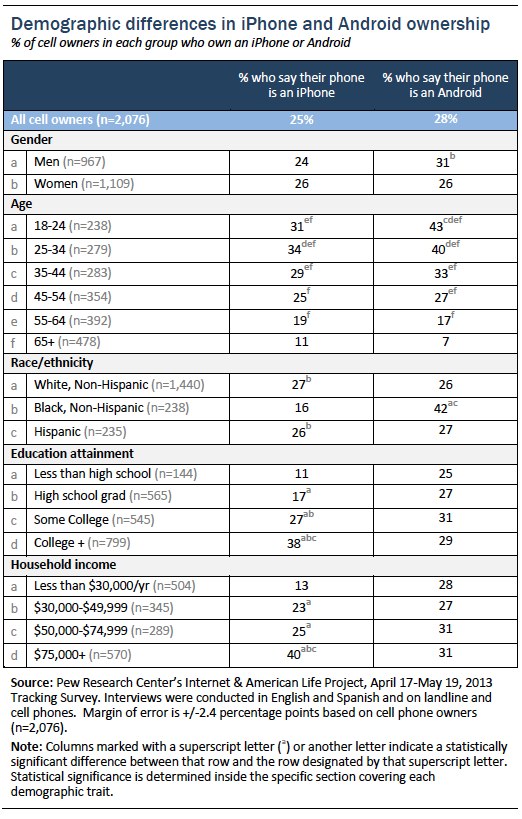
Android and iPhone owners are equally common within the cell owner population as a whole, although this ratio differs across various demographic groups. Cell phone owners from a wide range of educational and household income groupings have similar levels of Android adoption, but those from the upper end of the income and education spectrum are much more likely than those with lower income and educational levels to say they own an iPhone. Indeed, fully half—49%—of cell owners with a household income of $150,000 or more say their phone is an iPhone. And African-American cell owners are more likely than whites or Latinos to say that their phone is an Android device as opposed to an iPhone.
NOTES
1 This includes anyone who identified their phone as an iPhone, Android phone, Blackberry, or Windows phone
WWDC’s Software Announcements Are Apple’s Future

Samsung Galaxy S4 review: continuous improvements on the screen, camera and even the software
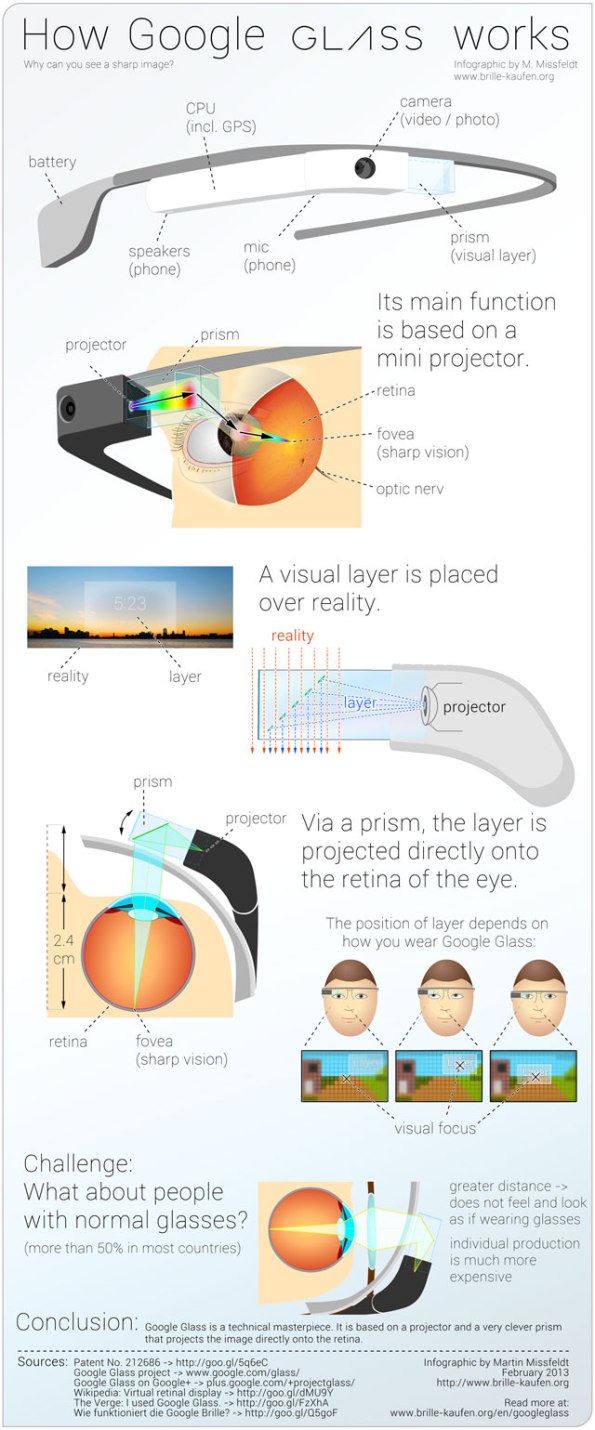
How Google Glass Works
Google Glass is an attempt to free data from desktop computers and portable devices like phones and tablets, and place it right in front of your eyes.
Essentially, Google Glass is a camera, display, touchpad, battery and microphone built into spectacle frames so that you can perch a display in your field of vision, film, take pictures, search and translate on the go.
The principle is one that has been around for years in science fiction, and more recently it’s become a slightly clunky reality. In fact, the “heads-up display” putting data in your field of vision became a reality as early as 1900 when the reflector sight was invented.
Here is how it works:
Will you get a pair for yourself? Share your thoughts in comments.